Secured and monitored web infrastructure
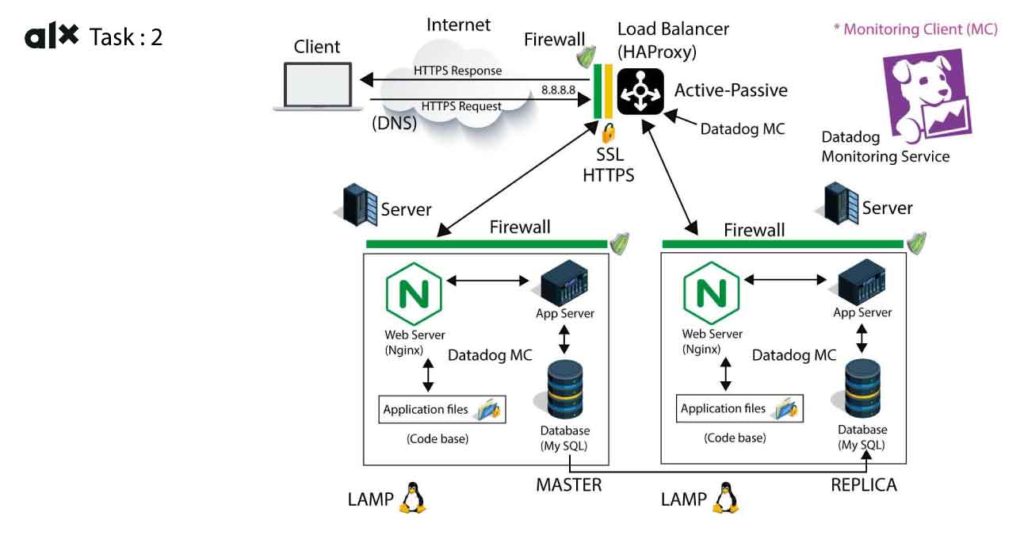
Why We Add Elements to the Infrastructure:
- Scalability: We add more elements to the infrastructure to handle increased demand. As more users visit our website or application, we need additional servers and resources to ensure everything runs smoothly.
- Redundancy: Elements like backup servers are added for redundancy. If one server fails, the backup can take over to prevent downtime.
What Firewalls Are For:
- Security: Firewalls are used to protect our infrastructure from unauthorized access and cyberattacks. They act like a barrier that filters incoming and outgoing traffic, allowing only approved data to pass through.
Why Traffic Served Over HTTPS:
- Encryption: HTTPS secures data in transit. It encrypts the information exchanged between a user’s browser and our servers, safeguarding sensitive data like login credentials and personal information.
What Monitoring Is Used For:
- Performance: Monitoring helps us keep an eye on the health of our infrastructure. We use it to detect issues, like server overloads or unusual activity, before they cause problems for users.
How Monitoring Collects Data:
- Data Collection Tools: Monitoring tools collect data through various sensors and agents installed on our servers. They continuously gather information about server performance, traffic, and other key metrics.
How to Monitor Web Server QPS:
- Check Monitoring Tools: To monitor web server Query Per Second (QPS), check the relevant metrics in your monitoring tool. This will show you how many queries your server is handling per second.
Issues with the Infrastructure:
Terminating SSL at the Load Balancer Level:
- Security Risk: Terminating SSL (decryption) at the load balancer can expose sensitive data. It’s safer to keep SSL encrypted end-to-end, from the user’s browser to the server.
Having Only One MySQL Server Accepting Writes:
- Single Point of Failure: If this server fails, it disrupts the entire system. Adding a failover or replication system would ensure data integrity and availability.
Having Servers with the Same Components:
- Uniformity Risk: If all servers have the same components, a vulnerability affecting one could affect all. Diverse configurations can enhance security and prevent a single point of failure.
